by AJ Gyomber | Jul 7, 2025 | Tech Tips
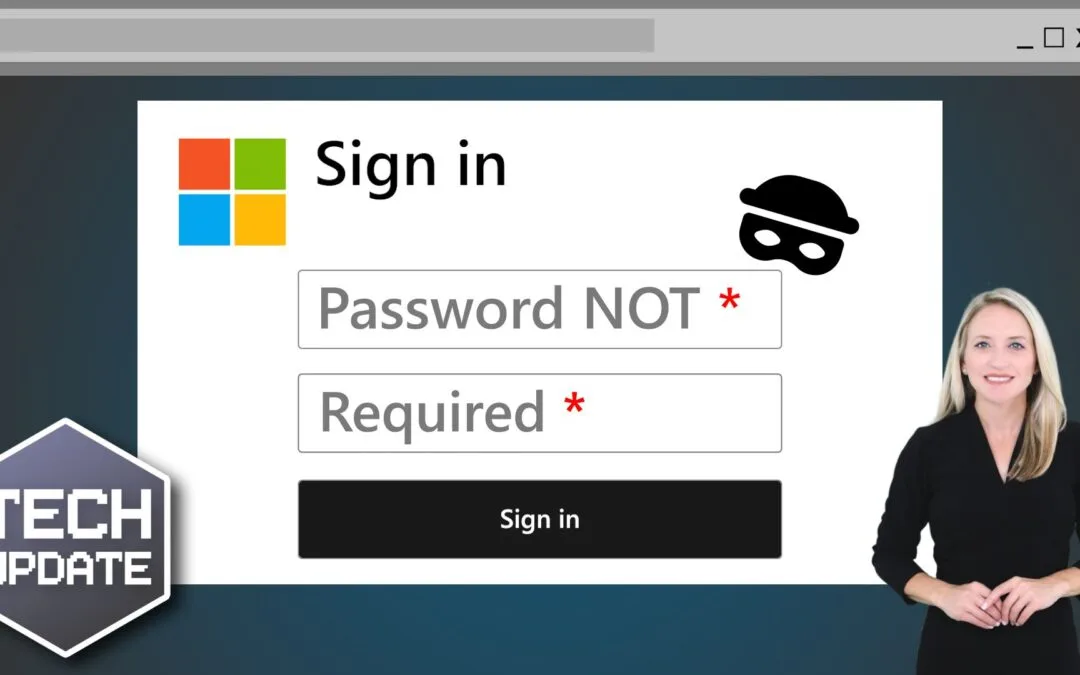
Have you ever felt like just when you’ve nailed your cybersecurity – BAM! – something new comes along to throw a spanner in the works? That’s exactly what’s happening right now. There’s a new scam doing the rounds. And it’s catching out businesses just like yours. The...

by AJ Gyomber | Jun 30, 2025 | Tech Tips
How many times have you tried searching for a file, only to forget what you called it? You know it’s there. You remember writing it, maybe even roughly when. But Windows search just stares blankly back at you. Or worse, throws up ten random web results and a document...
by AJ Gyomber | Jun 23, 2025 | Tech Tips
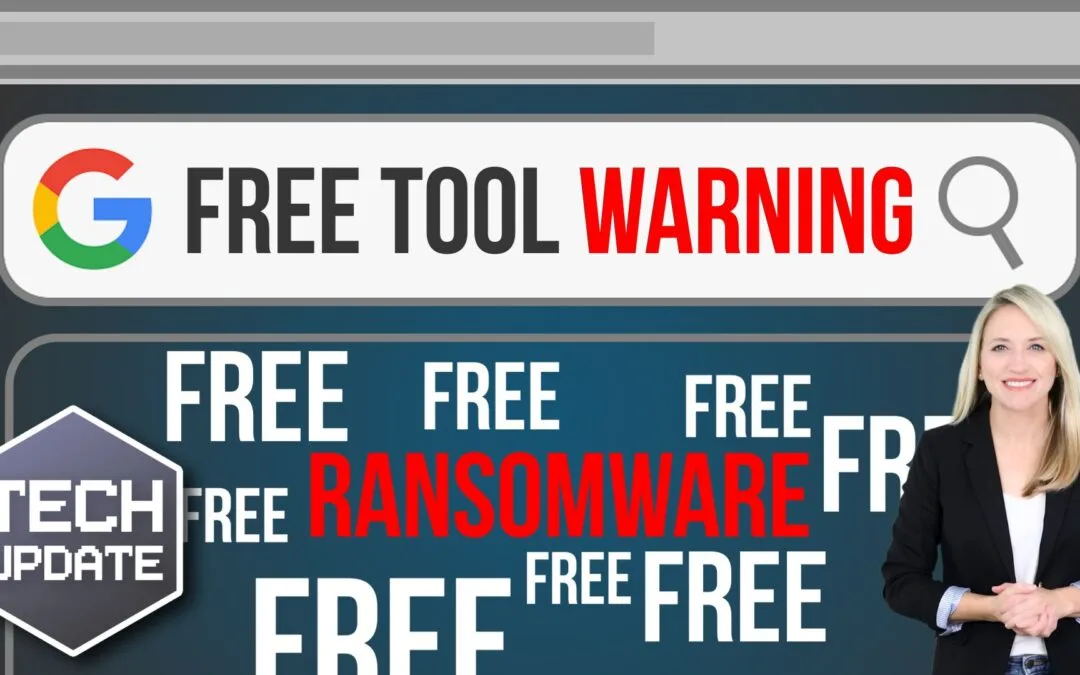
Ever needed to quickly convert a file, say, from a Word doc to a PDF? And found yourself Googling for a free tool to do it? It seems harmless enough, right? A quick download, a fast conversion, job done. But what if I told you that one small click could secretly open...

by AJ Gyomber | Jun 16, 2025 | Tech Tips
Have you ever sat in a Teams meeting and found yourself gritting your teeth every time someone said, “next slide, please”? Me too. And if your business runs a lot of online meetings or webinars, you’ll know the frustration of clunky handovers and awkward pauses when...

by AJ Gyomber | Jun 9, 2025 | Tech Tips
You trust your team, right? They’re smart, capable, and they know better than to click on suspicious links or open unexpected attachments. They already know that phishing emails look trustworthy on purpose. To trick them into giving away sensitive data or downloading...

by AJ Gyomber | Jun 2, 2025 | Tech Tips
Spreadsheets have been a go-to business tool for decades now. They’re familiar and easy to use (and if we’re being honest, we can all feel like a bit of a genius when we get that one formula to work, right?). The problem is, 90% of businesses are still relying on...

by AJ Gyomber | May 19, 2025 | Tech Tips
If you’ve ever used Incognito mode in Chrome, you probably know the basics: It lets you browse without saving your history, cookies, or other temporary data. But was it ever truly private? Not entirely… Until recently, if you copied something from an Incognito tab,...

by AJ Gyomber | May 12, 2025 | Tech Tips
Microsoft is really leaning into AI lately. And its latest idea is to make Copilot open automatically when you launch Microsoft Edge. Right now, if you want to use Copilot in Edge, you must click the little icon in the sidebar. No big deal. But the auto-open feature...

by AJ Gyomber | May 5, 2025 | Tech Tips
Do you feel like you’re constantly hearing about cyber attacks lately? You’re not imagining things. Cyber attacks are on the rise. And they’ve overtaken other risks as the number one concern for many businesses worldwide. From ransomware and data breaches to IT...

by AJ Gyomber | Apr 28, 2025 | Tech Tips
Weak passwords are one of the biggest security risks to your business. Why? Because cyber criminals are getting smarter than ever before. If they manage to crack just one password, they could gain access to your sensitive business data, financial information, or even...










